Setup GCP cloudrun deployment
GitHub Actions help in integrating CI/CD so you can test, build, deploy your code right from GitHub. In this post, we will set up a continuous CI/CD flow to deploy stateless containers from a specific branch in our repository. To learn the basics about GitHub actions, check out my previous post.
Steps to perform:
- Enable cloud build and cloud run API.
- Create a service account with the required permissions.
- Update secrets in the repository.
- Add cloud run.yml file.
- Push a commit to verify the deployment.
1. Enable cloud build and cloud run API.
Go to the GCP console and enable the cloud build and cloud run APIs in an existing project or newly created Google Cloud Project.
2. Create a service account with the required permissions.
What are service accounts?
A service account is a special kind of account used by an application or a virtual machine (VM) instance, not a person. Applications use service accounts to make authorized API calls, authorized as either the service account itself.
Now we need to create a service account that will authorize GCP related operations in Github actions.
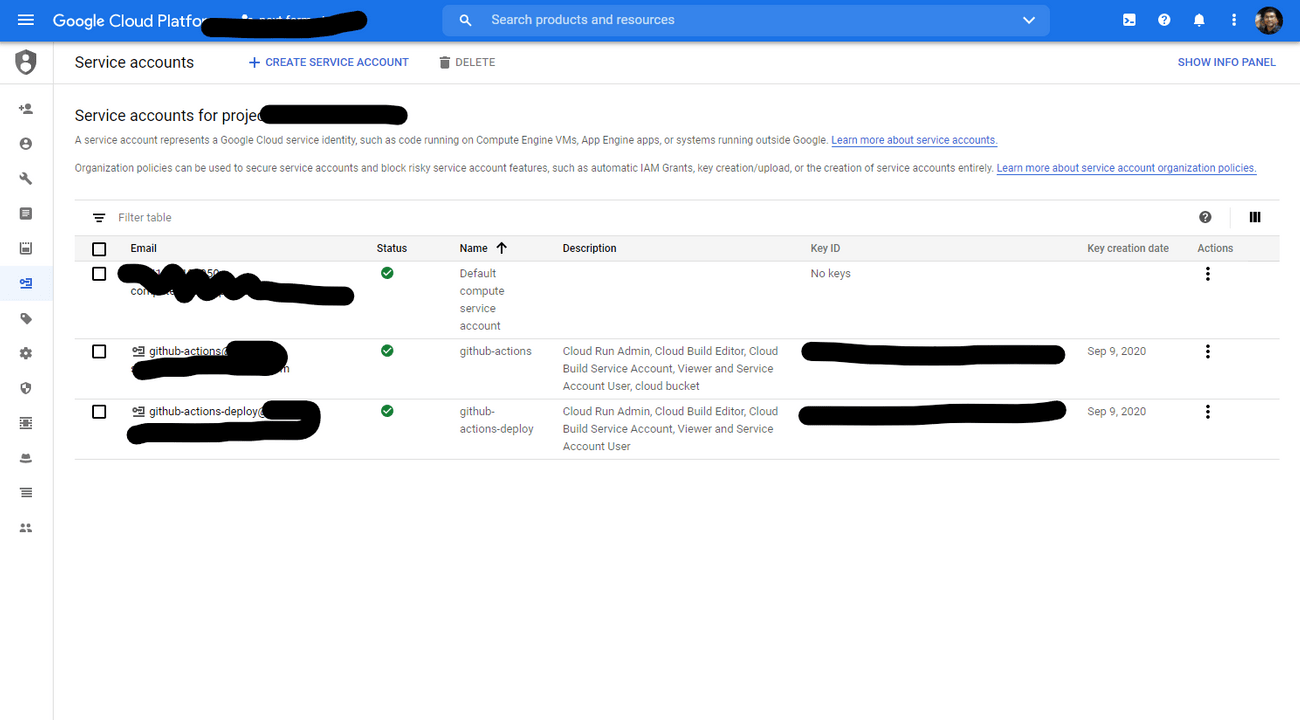
- Go to service accounts page in cloud console.
- Choose your project and Click Create Service Account.
- Enter a service account name, an optional description, select below roles, and then click Save.
Cloud Run Admin- allows for the creation of new servicesCloud Build Editor- allows for deploying cloud buildsCloud Build Service Account- allows for deploying cloud buildsViewer- allows for viewing the projectService Account User- required to deploy services to Cloud Run
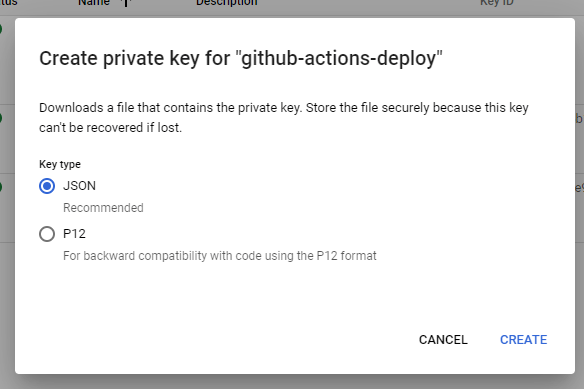
3. Update secrets in the repository.
After the SA creation, the account details need to be made available in GitHub action to authorize the build and deploy command. Click on the Actions menu, click on the create key, and then export the key in JSON format.
-
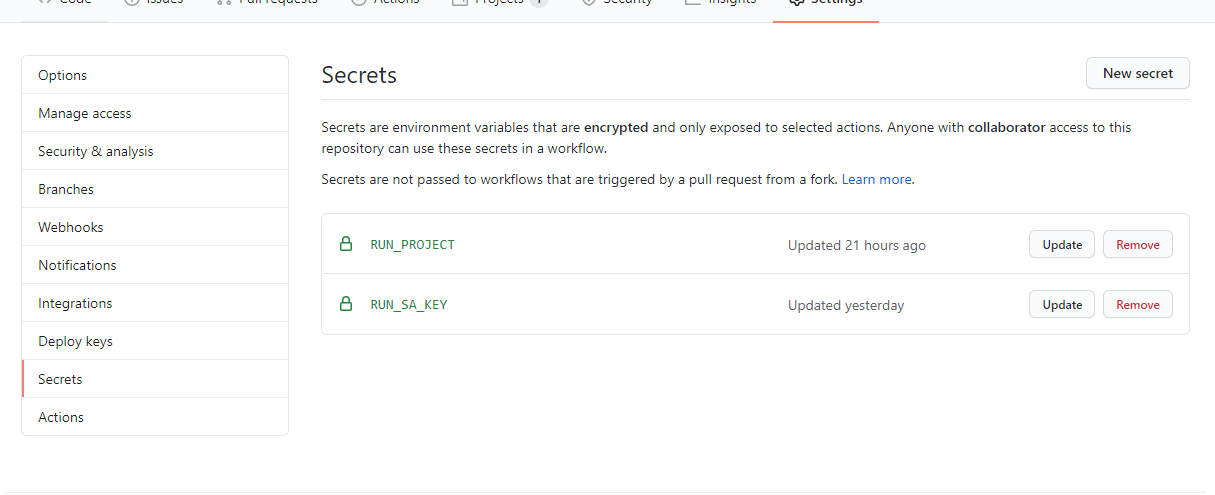
Navigate to the setting tab of your GitHub repository.
-
click on secrets and then New secret.
-
Name:
RUN_SA_KEYvalue: content of the exported JSON key. -
Name:
RUN_PROJECTvalue: GCP Project ID.(displayed in the Project Info section of the console dashboard)
-
4. Add cloud run.yml file.
Now, create cloudrun.yml file in .github/workflows/ folder and copy the below content to it. The file name can be anything, I am using cloudrun here.
name: Build and Deploy to Cloud Run
on:
push:
branches:
- canary
env:
PROJECT_ID: ${{ secrets.RUN_PROJECT }}
RUN_REGION: us-central1
SERVICE_NAME: sample-project
jobs:
setup-build-deploy:
name: Setup, Build, and Deploy
runs-on: ubuntu-latest
steps:
- name: Checkout
uses: actions/checkout@v2
# Setup gcloud CLI
- name: Setup gcloud CLI
uses: GoogleCloudPlatform/github-actions/setup-gcloud@master
with:
version: '290.0.1'
service_account_key: ${{ secrets.RUN_SA_KEY }}
project_id: ${{ secrets.RUN_PROJECT }}
# Build and push image to Google Container Registry
- name: Build and Push
run: |-
gcloud builds submit \
--quiet \
--tag "gcr.io/$PROJECT_ID/$SERVICE_NAME:$GITHUB_SHA"
# Deploy image to Cloud Run
- name: Deploy to Cloud Run
run: |-
gcloud run deploy "$SERVICE_NAME" \
--quiet \
--region "$RUN_REGION" \
--image "gcr.io/$PROJECT_ID/$SERVICE_NAME:$GITHUB_SHA" \
--platform "managed" \
--allow-unauthenticated
setup-build-deploy job has 4 steps.
Checkout- getting code from github repositorySetup gcloud CLI-setting up and authenticating with SA keyBuild and Push- trigger build in GCP cloud buildDeploy to Cloud Run- deploy the built image in cloud run
After successful execution, the container will be deployed in the cloud run.
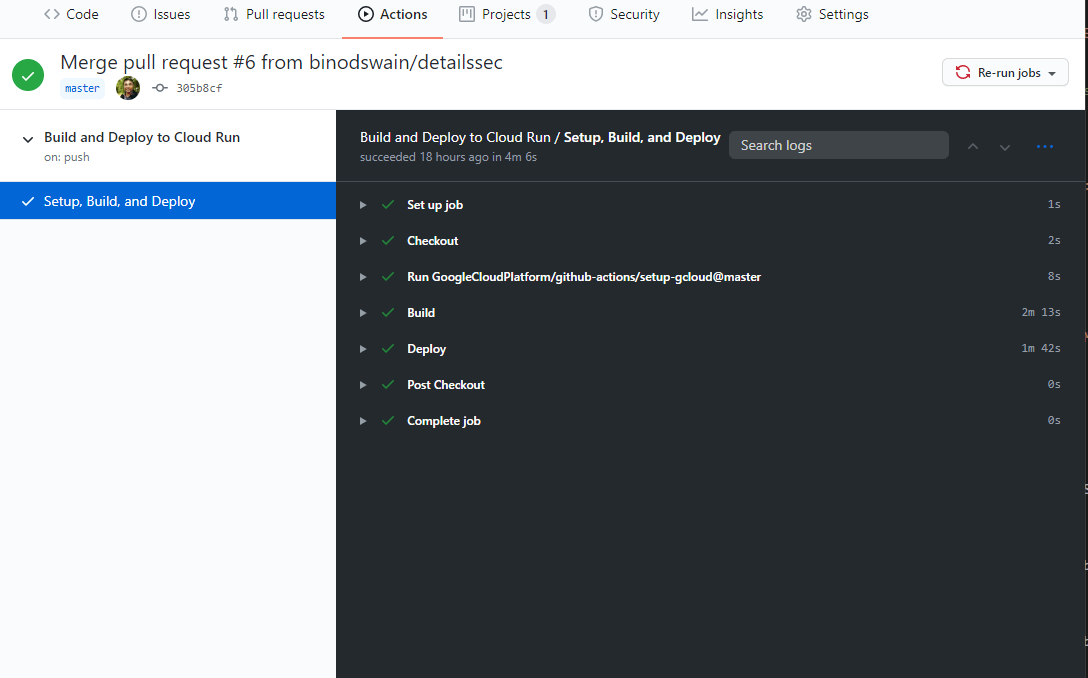
5. Push a commit to verify the deployment.
We have set up the action to get triggered on every push event in canary branch. Now add and commit your changes to the canary branch and check the execution in the Actions tab.
Additional step: Run a test/build task before executing setup-build-deploy
Add a test job and make the setup-build-deploy job depend on its execution status. If the job fails due to any test case or lint error, the setup-build-deploy will not execute.
name: Build and Deploy to Cloud Run
on:
push:
branches:
- canary
env:
PROJECT_ID: ${{ secrets.RUN_PROJECT }}
RUN_REGION: us-central1
SERVICE_NAME: sample-project
jobs:
test:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Running test
uses: actions/setup-node@v1
with:
node-version: '10.x'
- run: npm i
- run: npm test
env:
CI: true
setup-build-deploy:
name: Setup, Build, and Deploy
runs-on: ubuntu-latest
needs: test
steps:
- name: Checkout
uses: actions/checkout@v2
# Setup gcloud CLI
- name: Setup gcloud CLI
uses: GoogleCloudPlatform/github-actions/setup-gcloud@master
with:
version: '290.0.1'
service_account_key: ${{ secrets.RUN_SA_KEY }}
project_id: ${{ secrets.RUN_PROJECT }}
# Build and push image to Google Container Registry
- name: Build and Push
run: |-
gcloud builds submit \
--quiet \
--tag "gcr.io/$PROJECT_ID/$SERVICE_NAME:$GITHUB_SHA"
# Deploy image to Cloud Run
- name: Deploy to Cloud Run
run: |-
gcloud run deploy "$SERVICE_NAME" \
--quiet \
--region "$RUN_REGION" \
--image "gcr.io/$PROJECT_ID/$SERVICE_NAME:$GITHUB_SHA" \
--platform "managed" \
--allow-unauthenticated
More References:
- Workflow syntax for GitHub Actions.
- More usage example.
- Example Workflows for Github Actions with Google Cloud Platform